Course Description:
This course focuses on practical learning of computer hardware security using a hands-on approach. Students will perform a set of well-designed experiments on a custom-designed hardware platform, called HaHa, to understand innards of a computer system and ethically “hack” into it at different levels. They will examine it to understand security vulnerabilities, mount attacks, and implement various countermeasures to protect against specific attacks on hardware. The attacks the course covers are diverse in nature spanning various hardware components and life-cycle stages – they include reverse-engineering, counterfeiting/cloning, side-channel, fault-injection, and physical tampering (e.g., hardware Trojan, mod-chip) attacks.
The custom-designed hardware platform is called Hardware Hacking board (HaHa). It is an experimental development board for teaching and learning on diverse aspects of hardware security. The board currently has the capacity to support over a dozen experiments (provided below) that recreate different types of hardware security fundamentals, attacks, and countermeasures used in their defense for learning all major aspects of hardware security. Some versions of the HaHa board can be fabricated using the design files publicly available through this website (as well as the Hands-on Hardware Security Book website) or can be acquired from third-party vendors.
The HaHa board and 19 experiments (including Experiment 0) designed to run on it have been developed by Prof. Swarup Bhunia with help of his students and collaborators, at the Electrical and Computer Engineering Department of University of Florida, where the Hands-on Hardware Security course is being offered each fall for past five years.
The experiments can be run on the HaHa board by connecting it to a computer and without need of any additional benchtop electrical measurement unit. Hence, this course is suitable for online learning since it does not require access to a physical lab. Note that few experiments, however, (e.g., Experiment 9) require access to a USB Oscilloscope, such as Analog Discovery 2. Instructors are welcome to choose any subset of these experiments into their offered course depending on course duration and other factors.
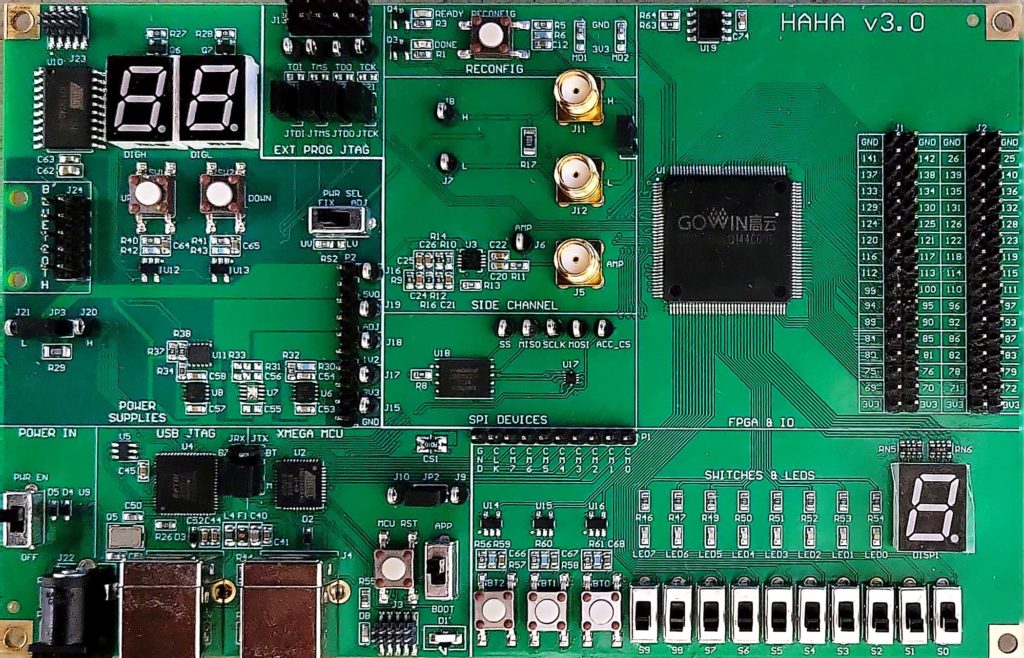
Included Devices
- GOWIN GW1N-9 (GW1N-UV9LQ144C6/I5 ver. C) FPGA
- Atmel ATxmega16A4U Microcontroller
Helpful Guides:
- Software Installation Instructions for Windows
- Software Installation Instructions for Linux
- GOWIN FPGA Guide
- Xmega Microcontroller Guide
- Frequently Asked Questions (FAQs)
Helpful Codes:
- Helpful Codes
- Ubuntu Helpful Codes (for running FPGA/microcontroller programming softwares)
- Gowin Pin Assignments
- Ubuntu OVA File (for software experiments)
- Password: pass123!
Hands-on Experiments:
- Experiment 0: Learning the HaHa Platform (Suggested Duration: One Week)
- Experiment 1: Buffer Overflow (Suggested Duration: One Week)
- Experiment 2: Information Security: Encryption/Decryption (Suggested Duration: One Week)
- Experiment 3: Bus Snooping Attacks (Suggested Duration: One Week)
- Experiments 4 and 5: Hardware Trojan Attacks (Suggested Duration: Two Weeks)
- Experiment 6: Reverse Engineering Attacks (Suggested Duration: One to Two Weeks)
- Experiment 7: Hardware-Based Security Primitives (PUFs and TRNGs) (Suggested Duration: Two To Three Weeks)
- Experiment 8: Modchip Attacks (Suggested Duration: One Week)
- Experiment 9: Side Channel (Power) Attacks (Suggested Duration: Two Weeks)
- Experiment 10: Fault Injection Attacks (Suggested Duration: One Week)
- Experiment 14: Hardware Obfuscation and Logic Locking (Suggested Duration: One Week)
- Experiment 16: Oracle-Based Attacks (Suggested Duration: Two Weeks)
- Experiment 17: Scan Chain Protection (Suggested Duration: Two Weeks)
- Experiment 18: Hardware Watermarking (Suggested Duration: Two Weeks)
Developers and Contributors:
- Reiner Dizon-Paradis
- Rohan Reddy Kalavakonda
- Dr. Shuo Yang
- Pravin Gaikwad
- Christopher Vega
- Miles F Mulet
- Dr. Yier Jin
- Dr. Swarup Bhunia
References
Yang, Shuo; Paul, Shubhra Deb; Bhunia, Swarup
Hands-on Learning of Hardware and Systems Security Journal Article
In: ASEE, vol. 9, no. 2, pp. 1-25, 2021.
@article{Yang2021HandsOn,
title = {Hands-on Learning of Hardware and Systems Security},
author = {Shuo Yang and Shubhra Deb Paul and Swarup Bhunia},
url = {https://advances.asee.org/hands-on-learning-of-hardware-and-systems-security/
https://drive.google.com/file/d/1CQBGZnjjRzIG98iXiKTInjkveGcK_UdN/view},
year = {2021},
date = {2021-04-01},
journal = {ASEE},
volume = {9},
number = {2},
pages = {1-25},
abstract = {Hardware security is one of the most researched areas in the field of security. It focuses on discovering and understanding attacks and countermeasures for electronic hardware that provides the “root-of-trust” for modern computing systems upon which the software stack is built. The increasing reliance on electronic devices in our everyday life has also escalated the risks of experiencing security threats on these technologies. Students today are exposed to these devices and thus require a hands-on learning experience to be aware of the threats, solutions, and future research challenges in hardware security. Currently, there are limited opportunities for students to learn and understand hardware security. A significant factor limiting exposure to these topics is the lack of an accessible, low-cost, flexible, and ready-made platform for training students on the innards of a computing system and the spectrum of security issues/solutions at the hardware-level. In this paper, we introduce the motivation and efforts behind a course named “Hands-on Hardware Security.” The Department of Electrical and Computer Engineering at the University of Florida has been offering this course for the past three years in providing experiential learning of hardware security through a set of well-designed experiments performed on a custom hardware module. We also present, in detail, the idea of a custom-designed, easy-to-understand, flexible hardware module with fundamental building blocks that can emulate a computer system and create a network of connected devices. We refer to the module as “HaHa SEP” (Hardware Hacking Security Education Platform), and it encourages students to learn and exercise “ethical hacking,” a critical concept in the hardware security field. It is the first and only known lab course offered online, where students can perform ethical hacking of a computing system using a dedicated hardware module. This paper also provides a brief introduction to the experiments performed using this module, highlighting their significance in the field of Hardware Security. Finally, it concludes with a compilation of course evaluation survey results discussing the success of this course in engaging students’ interest in the subject matter and determining the accomplishment of maintaining a balance between their expectation and the effort required towards the course.},
keywords = {},
pubstate = {published},
tppubtype = {article}
}
Acknowledgement
The development of the HaHa educational platform and the Hands-on Hardware Security experiments was supported in part by National Science Foundation (NSF) through grants 1603480 – TUES:Type1:Collaborative: An Integrative Hands-on Approach to Security Education for Undergraduate Students, and 1623310 – Collaborative: HACE Lab: An Online Hardware Security Attack and Countermeasure Evaluation Lab.
We expect the instructors, students, and practitioners using the materials provided in this page will appropriately acknowledge the developers, contributors, and sponsors.
Copyright Notices
The course materials are made available here for educational purposes and users need to follow academic fair use policy.
Video Demo of Experiment 3 (Bus Snooping Attacks)
By: Lakshmikavya Kalyanam, University of South Florida
Video Demo of Experiment 4 (Hardware Trojan Attacks I)
By: Luke Morreale and Bardia Nadimi, University of South Florida
Video Demo of Experiment 8 (Modchip Attacks)
By: Mateus Augusto Fernandes Amador and Samir Ahmed Ona, University of South Florida