By: Abdulrahman Alaql, Xinmu Wang, Md Moshiur Rahman, and Swarup Bhunia
Stage: Security Analysis of Gate-Level Netlist Obfuscation
Summary
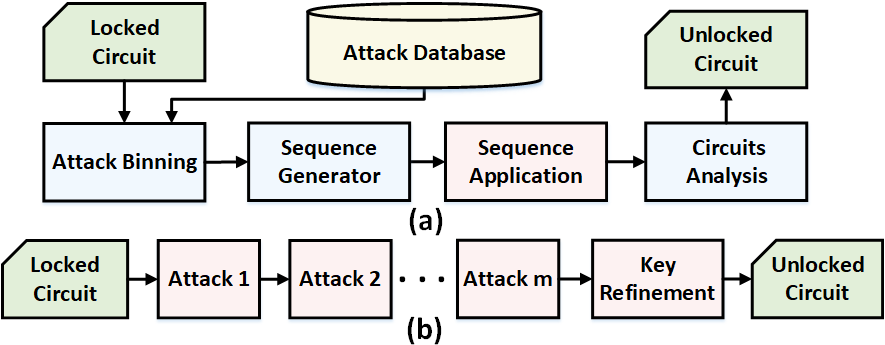
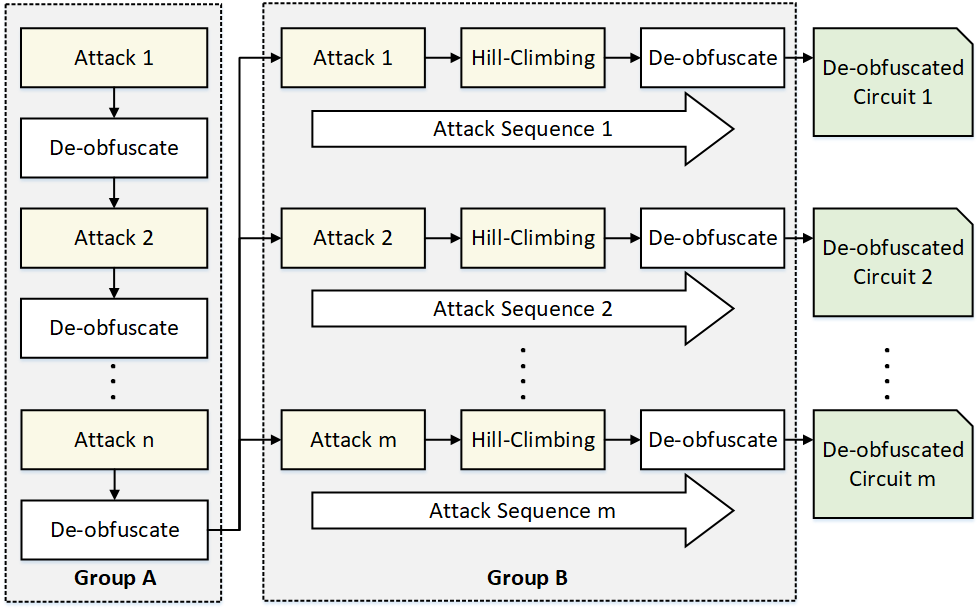
- We introduce a novel combined attack modality, referred to as SOMA, which relies on judiciously combining the existing attacks to produce a significantly more powerful one.
- We demonstrate that such an attack can expose hidden exploits and measure the level of security offered by a given obfuscation technique.
- SOMA creates a sequence of attacks, where the outcome of each attack is used to guide the next and concludes with a key-refinement measure to restore the functionality of a locked IP.
- We demonstrate that SOMA can easily break major existing locking schemes that are believed to be secure with an attack accuracy average of 94.88%.
Contact
Input/Output Interface
- Input: Locked Circuit (bench format)
- Output: Key Extraction Report.
Dependencies
- ABC Compiler.
- Synopsys VCS.
Licensing Info
For educational use only.