By: Abdulrahman Alaql, Xinmu Wang, Md Moshiur Rahman, and Swarup Bhunia
Stage: Security Analysis of Gate-Level Netlist Obfuscation
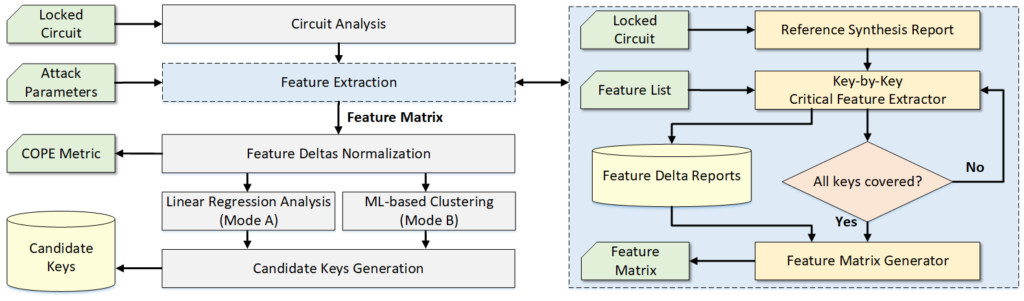
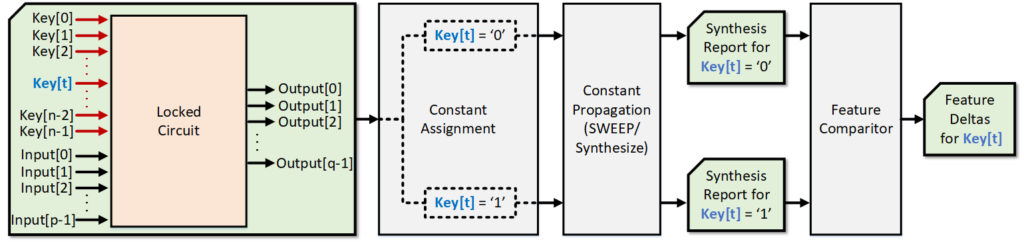
Summary
- SCOPE is a synthesis-based constant propagation attack for security evaluation of logic locking techniques.
- The attack is oracle-less and requires minimal knowledge from the attacker’s point of view.
- The introduced attack performs a synthesis-based analysis on each individual key-input port and looks for meaningful design features that may help point to the correct key value.
- SCOPE offers two attack modes: a linear regression test and an unsupervised machine-learning analysis.
Contact
Input/Output Interface
- Input: Locked Circuit (bench format)
- Output: Key Extraction Report.
Dependencies
- ABC Compiler.
Licensing Info
For educational use only.