By: Yujie Wang (ICT, Chinese Academy of Sciences), Pu Chen (Alexa Shopping, Amazon Web Services), Jiang Hu (Texas A&M University), Guofeng Li (Nankai University), and JV Rajendran (Texas A&M University)
Stage: Physical Design and Manufacturing
Summary
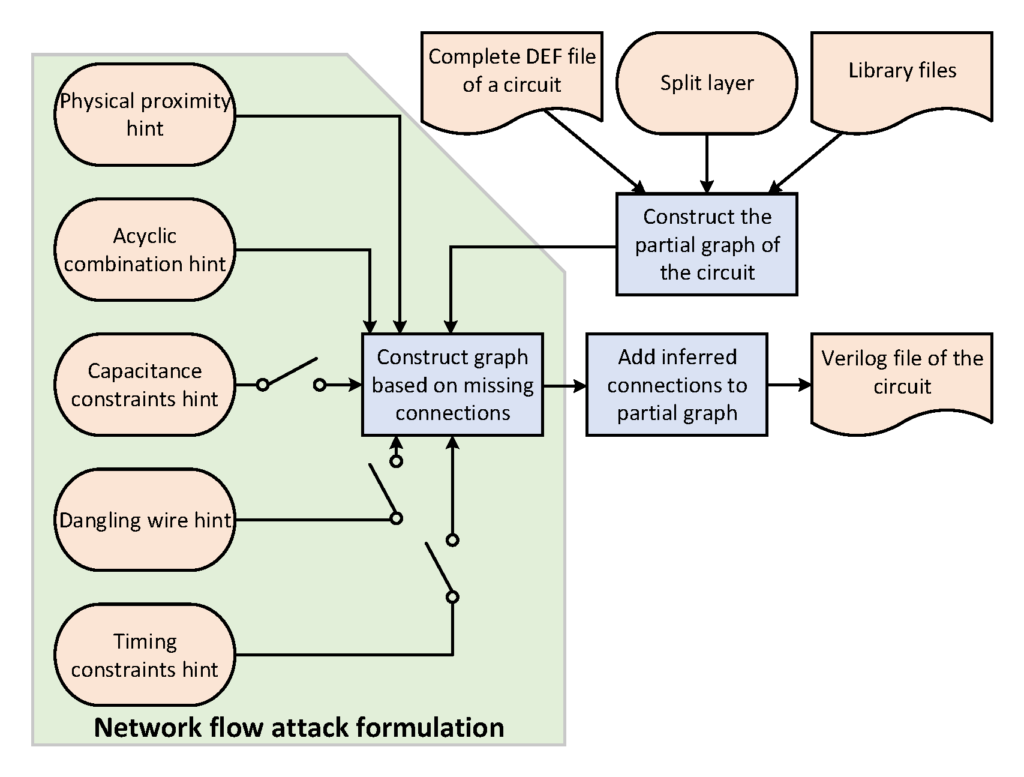
The network flow attack for split manufacturing is an attack for recovering the missing connections in the partial design of a circuit. It is written in Python. Given a DEF file for a circuit, the layer that the circuit is split at, and the appropriate library files, the tool returns a verilog file for the circuit after inferring the missing connections. The tool uses five hints and formulates the problem of finding the missing connections as a network flow problem. The five hints are (1) physical proximity, (2) acyclic combination, (3) capacitance constraints (4) direction of dangling wire, and (5) timing constraints. The tool also provides flexibility whether or not to use the last three hints independently i.e., one can use any of the 2^3 combinations of the last three hints. The solution of the network flow problem is translated into inference about the missing connections using which an attacker can get the complete design of the circuit.
Contact
JV Rajendran and Vasudev Gohil
Input/Output Interface
- Input: DEF file of the circuit, split layer, attack hints to use
- Output: Attacked verilog file of the circuit with missing connections added
Dependencies
Python 3.6 or above
References
The Cat and Mouse in Split Manufacturing Journal Article
In: IEEE Transactions on Very Large Scale Integration (VLSI) Systems, vol. 26, no. 5, pp. 805-817, 2018, ISSN: 1557-9999.
Acknowledgments
- This work was supported in part by NSF under Grant CCF-1618824 and in part by SRC under Grant 2016- TS-2688 and Grant 2016-TS-2689. The work of Y. Wang was supported by the China Scholarship Council