By: Rajat Subhra Chakraborty, Francis Wolff, Somnath Paul, Christos Papachristou, and Swarup Bhunia
Stage: Production and Test
Summary
In order to ensure trusted in–field operation of integrated circuits, it is important to develop efficient low–cost techniques to detect malicious tampering (also referred to as Hardware Trojan) that causes an undesired change in functional behavior.
Conventional post-manufacturing testing, test generation algorithms and test coverage metrics cannot be readily extended to hardware Trojan detection.
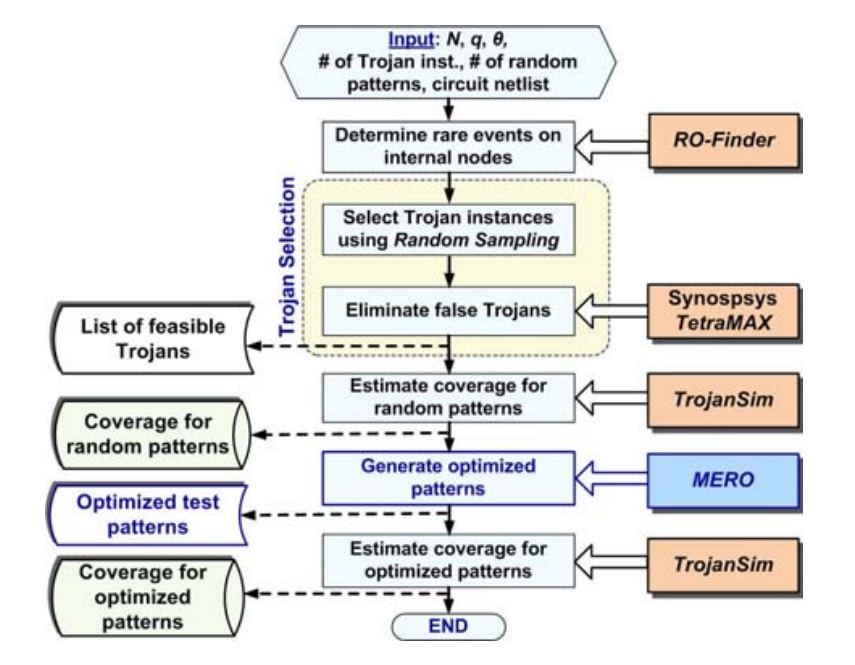
MERO is a statistical test generation tool written in C for generating a corpus of logic test patterns aimed at maximizing the Trigger and Trojan Coverage of a sampled potential Trojan population for a given gate-level design. MERO uses N-detect testing to ensure each Trojan from the sampled Trojan population can be triggered at least N times. The resulting test patterns can be used to detect potential Trojans after design fabrication through functional testing.
Contact
Input/Output Interface
- Input: Gate-level Netlist (Verilog)
- Output: Test Patterns
Dependencies
Onespin -or- Synopsys TetraMAX -or- JasperGold
Licensing Info
Copyright 2020 University of Florida. Please contact aarranz@ufl.edu for licensing options.
References
MERO: A Statistical Approach for Hardware Trojan Detection Proceedings Article
In: Clavier, Christophe; Gaj, Kris (Ed.): Cryptographic Hardware and Embedded Systems - CHES 2009, pp. 396-410, Springer Berlin Heidelberg, Berlin, Heidelberg, 2009, ISBN: 978-3-642-04138-9.