By: Tamzidul Hoque (University of Kansas), Mahmudul Hasan (University of Kansas), Jonathan Cruz (University of Florida), Prabuddha Chakraborty (University of Florida), and Swarup Bhunia (University of Florida)
Stage: RTL, HDL, Gate-Level, IC Fabrication
Summary
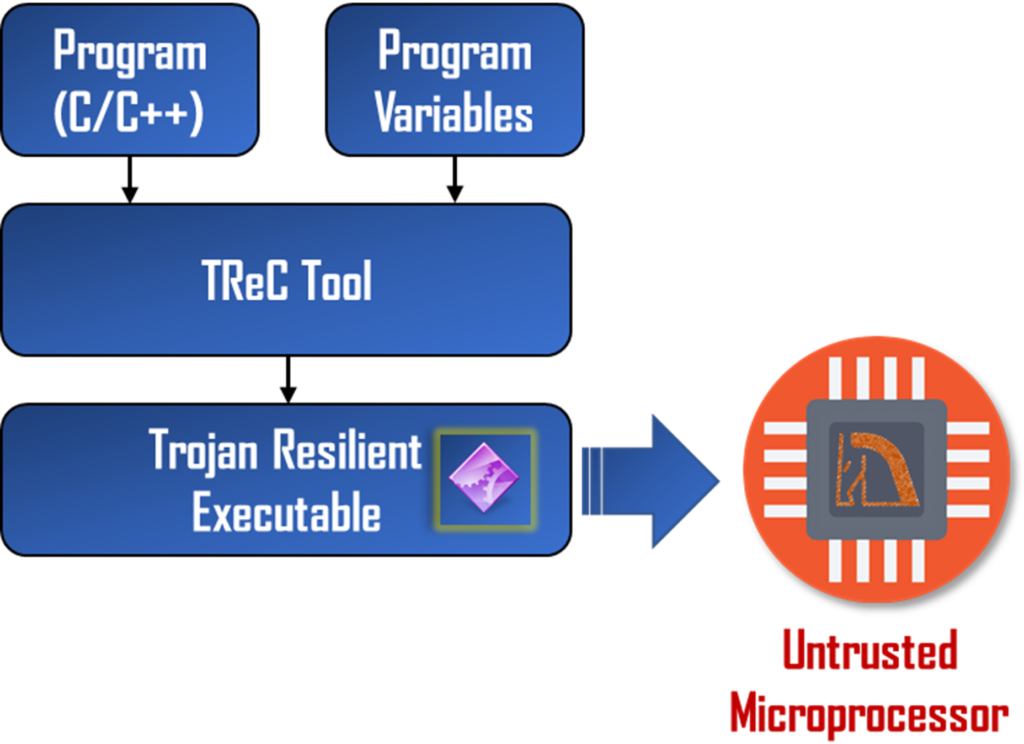
TReC is a purely software-centric solution to enable Trojan Resilient Computing in microprocessors during field operation against Trojans that corrupt the critical program outputs (i.e., variables). The tool takes a software program (C/C++) to be executed on the untrusted processor and transforms it with Trojan-resilient properties. This solution is particularly attractive for the commercial off-the-shelf (COTS) microprocessors. COTS based system design ecosystem provides an attractive system design paradigm due to the drastically shorter deployment cycle and reduced development cost compared to custom solutions. However, there is a growing concern of security vulnerabilities in COTS components arising from embedded malicious logic, or hardware Trojans. Existing trust-verification approaches are typically not applicable to COTS hardware due to the absence of golden models and lack of observability of internal signals. Hence, TReC can be utilized for protection against Trojan attacks at runtime.
Contact
Input/Output Interface
- Input: A target program to be protected (C/C++), program variables to be protected, other configuration parameters
- Output: An executable code that can detect and tolerate an alteration of the program variables
Dependencies
LLVM compiler, Python Libraries
Licensing Info
Available through licensing
References
TReC: Trojan-Resilient Computing in Untrusted Processors using Software Variants Conference
GOMACTech-2020 Conference, 2020.