By: Michael Zuzak (University of Maryland, College Park) and Ankur Srivastava (University of Maryland, College Park)
Stage: RTL, HDL
Summary
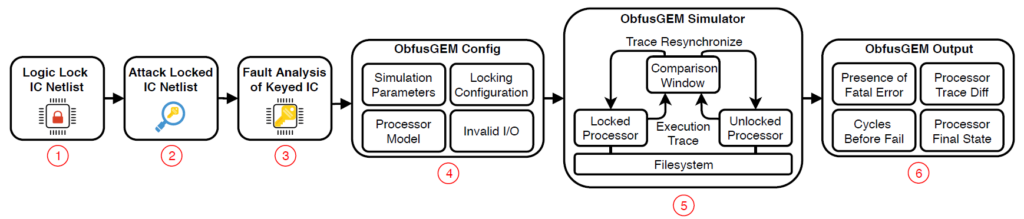
ObfusGEM is a comprehensive logic locking simulator designed to evaluate the supply-chain security of locked processor models. It implements an error injection framework inspired by the architectural error resilience community to “close the loop” between module-level logic locking or hardware security techniques and their application and architecture-level impact. We provide a library of existing hardware security techniques and configurations along with a simulation framework in hopes of providing a tool enabling the design and evaluation of hardware security configurations for specific processor architectures or devices.
Contact
Input/Output Interface
- Input: GEM5 Processor Model, Disk Image, Processor Applications, Logic Locking Configuration
- Output: Failure Rate of Application, Time to Failure for Application, Failure State for Application
Dependencies
- g++ version 4.8 or newer or clang version 3.1 or newer
- Python, version 2.6 – 2.7
- SCons, version 0.98.1 or newer
- zlib, any recent version
- m4, the macro processor
- protobuf, version 2.1 or newer
- pydot
- Perl
Licensing Info
BSD-3-Clause License
References
ObfusGEM: Enhancing Processor Design Obfuscation Through Security-Aware On-Chip Memory and Data Path Design Proceedings Article
In: International Symposium on Memory Systems (MEMSYS), 2020.
The Gem5 Simulator Journal Article
In: SIGARCH Comput. Archit. News, vol. 39, no. 2, pp. 1–7, 2011, ISSN: 0163-5964.
Acknowledgments
- This work was supported by the ARCS Foundation, the National Science Foundation (NSF) Grant 1642424, and the Air Force Office of Scientific Research Grant FA9550-14-1-0351