By: Zhaoxiang Liu, Yier Jin, and Xiaolong Guo
Stage: RTL

Summary
- A scalable framework that statically identifies threats in SoC platforms at RT-Level.
- By parsing HDL into an AST, more information can be used for tracking, identification, and localization of anomalies.
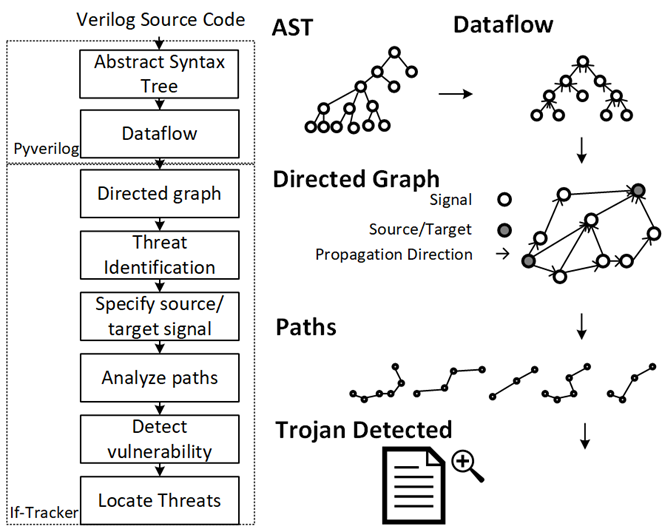
- A CAD tool that can parse Verilog HDL and automates security checks on the design. It models an SoC into a data-flow graph and automatically infers interactions between IP cores.
Contact
Input/Output Interface
- Input: Denoted Verilog program
- Output: Identify anomalies among IPs that can bypass individual security checks
Dependencies
- PyVerilog
- Icarus Verilog
- QIF-Verilog
Binariey
-
Instruction: Run on linux command: ./if-tracker –help
References
Liu, Zhaoxiang; Arias, Orlando; Fu, Weimin; Jin, Yier; Guo, Xiaolong
Inter-IP malicious modification detection through static information flow tracking Proceedings
2022 Design, Automation & Test in Europe Conference & Exhibition (DATE), 0000, ISBN: pp. 600-603.
@proceedings{IFtracker-Liu,
title = {Inter-IP malicious modification detection through static information flow tracking},
author = {Zhaoxiang Liu and Orlando Arias and Weimin Fu and Yier Jin and Xiaolong Guo},
isbn = {pp. 600-603},
howpublished = {2022 Design, Automation & Test in Europe Conference & Exhibition (DATE)},
keywords = {},
pubstate = {published},
tppubtype = {proceedings}
}
Acknowledgments
- This work is partially supported by the National Science Foundation (CCF-2019310, CCF-2028910).